According to a Project PM announcement, here are some of the 'classified intelligence' details about Romas/COIN (Odyssey) with capabilities to monitor and automatically analyze millions of conversations, and then secretly store a wide range of personal data. It appears as if even Apple, Google, and Disney's Pixar were trying to be brought aboard to help out in this mass surveillance apparatus.
Updated note: To be clear, all analysis and documentation to expose this mass surveillance was done by Project PM.
If you are not sitting, please do so. Although I don't advocate drinking, you might also pour a double-shot of whiskey to prepare yourself for distinctly unpleasant news about immensely sophisticated mass surveillance called Romas/COIN, or soon to be replaced by a similar program known as Odyssey. The nature and extent of the "counter intelligence" operation can be glimpsed in part by closely inspecting hundreds of e-mails among the 70,000 that were stolen in February from the contracting firm HBGary Federal.
After searching through HBGary e-mails for keywords and reading until I wanted to puke or scream, I decided to go ahead and run with Project PM's announcement. Barrett Brown of Project PM will publish these findings in full on Project PM Wiki later, but this is part of that release. According to Project PM:
For at least two years, the U.S. has been conducting a secretive and immensely sophisticated campaign of mass surveillance and data mining against the Arab world, allowing the intelligence community to monitor the habits, conversations, and activity of millions of individuals at once. And with an upgrade (Odyssey) scheduled for later this year, the top contender to win the federal contract and thus take over the program is a team of about a dozen companies which were brought together in large part by Aaron Barr - the same disgraced CEO who resigned from his own firm earlier this year after he was discovered to have planned a full-scale information war against political activists at the behest of corporate clients. The new revelation provides for a disturbing picture, particularly when viewed in a wider context. Unprecedented surveillance capabilities are being produced by an industry that works in secret on applications that are nonetheless funded by the American public - and which in some cases are used against that very same public. Their products are developed on demand for an intelligence community that is not subject to Congressional oversight and which has been repeatedly shown to have misused its existing powers in ways that violate U.S. law as well as American ideals.
Although military contractor Northrop Grumman had long held the contract for Romas/COIN, enter HBGary Federal CEO Aaron Barr in an email to Al Pisani, an executive at the much larger federal contractor TASC, with a plan related to COIN. "I met with [Mantech CEO] Bob Frisbie the other day to catch up. He is looking to expand a capability in IO [information operations] related to the COIN re-compete but more for DoD."
The layout and story is extremely long, and you'll need to read over the announcement at Project PM when it's published there. Project PM determined from the dozens of clues and references in leaked emails the unbelievable mass spying nature of Romas/COIN:
- Mobile phone software and applications constitute a major component of the program.
- There's discussion of bringing in a "gaming developer," apparently at the behest of Barr, who mentions that the team could make good use of "a social gaming company maybe like zynga, gameloft, etc." Lovegrove elsewhere notes: "I know a couple of small gaming companies at MIT that might fit the bill."
- Apple and Google were active team partners, and AT&T may have been as well. The latter is known to have provided the NSA free reign over customer communications (and was in turn protected by a bill granting them retroactive immunity from lawsuits). Google itself is the only company to have received a "Hostile to Privacy" rating from Privacy International. Apple is currently being investigated by Congress after the iPhone was revealed to compile user location data in a way that differs from other mobile phones; the company has claimed this to have been a "bug."
- The program makes use of several providers of "linguistic services." At one point, the team discusses hiring a military-trained Arabic linguist. Elsewhere, Barr writes: "I feel confident I can get you a ringer for Farsi if they are still interested in Farsi (we need to find that out). These linguists are not only going to be developing new content but also meeting with folks, so they have to have native or near native proficiency and have to have the cultural relevance as well."
- Alterion and SocialEyez are listed as "businesses to contact." The former specializes in "social media monitoring tools." The latter uses "sophisticated natural language processing methodology" in order to "process tens of millions of multi-lingual conversations daily" while also employing "researchers and media analysts on the ground;" its website also notes that "Millions of people around the globe are now networked as never before - exchanging information and ideas, forming opinions, and speaking their minds about everything from politics to products."
- At one point, TASC exec Chris Clair asks Aaron and others, "Can we name COIN Saif? Saif is the sword an Arab executioner uses when they decapitate criminals. I can think of a few cool brands for this."
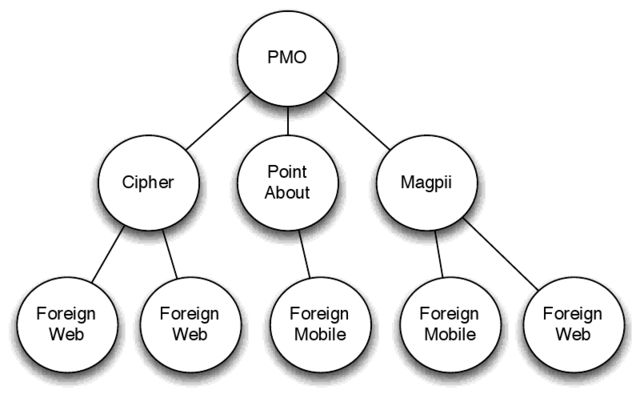
- A diagram attached to one of Barr's e-mails to the group depicts Magpii as interacting in some unspecified manner with "Foreign Mobile" and "Foreign Web." Magpii is a project of Barr's own creation which stands for "Magnify Personal Identifying Information," involves social networking, and is designed for the purpose of storing personal information on users. Although details are difficult to determine from references in Barr's e-mails, he discusses the project almost exclusively with members of military intelligence to which he was pitching the idea.
- There are sporadic references such things as "semantic analysis," "Latent Semantic Indexing," "specialized linguistics," and OPS, a programming language designed for solving problems using expert systems.
- Barr asks the team's partner at Apple, Andy Kemp (whose signature lists him as being from the company's Homeland Defense/National Programs division), to provide him "a contact at Pixar/Disney."
Altogether, then, a successful bid for the relevant contract was seen to require the combined capabilities of perhaps a dozen firms - capabilities whereby millions of conversations can be monitored and automatically analyzed, whereby a wide range of personal data can be obtained and stored in secret, and whereby some unknown degree of information can be released to a given population through a variety of means and without any hint that the actual source is U.S. military intelligence. All this is merely in addition to whichever additional capabilities are not evident from the limited description available, with the program as a whole presumably being operated in conjunction with other surveillance and propaganda assets controlled by the U.S. and its partners.
Here's the team players:
- TASC (PMO, creative services)
- HB Gary (Strategy, planning, PMO)
- Akamai (infrastructure)
- Archimedes Global (Specialized linguistics, strategy, planning)
- Acclaim Technical Services (specialized linguistics)
- Mission Essential Personnel (linguistic services)
- Cipher (strategy, planning operations)
- PointAbout (rapid mobile application development, list of strategic partners)
- Google (strategy, mobile application and platform development - long list of strategic partners)
- Apple (mobile and desktop platform, application assistance -long list of strategic partners)
- We are trying to schedule an interview with AT&T plus some other small app developers.
Two days after a briefing requirement meeting, the servers of HBGary and HBGary Federal were hacked by a small team of Anonymous operatives in retaliation for Barr's boasts to Financial Times that he had identified the movement's "leadership;" 70,000 e-mails were thereafter released onto the Internet. Barr resigned a few weeks later.
Also according to Project PM, along with clues as to the nature of COIN and its scheduled replacement, a close study of the HBGary e-mails also provide reasons to be concerned with the fact that such things are being developed and deployed in the way that they are. In addition to being the driving force behind the COIN recompete, Barr was also at the center of a series of conspiracies by which his own company and two others hired out their collective capabilities for use by corporations that sought to destroy their political enemies by clandestine and dishonest means, some of which appear to be illegal. None of the companies involved have been investigated; a proposed Congressional inquiry was denied by the committee chair, noting that it was the Justice Department's decision as to whether to investigate, even though it was the Justice Department itself that made the initial introductions. Those in the intelligence contracting industry who believe themselves above the law are entirely correct.
That such firms will continue to target the public with advanced information warfare capabilities on behalf of major corporations is by itself an extraordinary danger to mankind as a whole, particularly insomuch as that such capabilities are becoming more effective while remaining largely unknown outside of the intelligence industry. But a far greater danger is posed by the practice of arming small and unaccountable groups of state and military personnel with a set of tools by which to achieve better and better "situational awareness" on entire populations while also being able to manipulate the information flow in such a way as to deceive those same populations. The idea that such power can be wielded without being misused is contradicted by even a brief review of history.
History also demonstrates that the state will claim such powers as a necessity in fighting some considerable threat; the U.S. has defended its recent expansion of powers by claiming they will only be deployed to fight terrorism and will never be used against American civilians. This is cold comfort for those in the Arab world who are aware of the long history of U.S. material support for regimes they find convenient, including those of Saddam Hussein, Hosni Mubarak, and the House of Saud. Nor should Americans be comforted by such promises from a government that has no way of ensuring that they will be kept; it was just a few months ago that a U.S. general in Afghanistan ordered a military intelligence unit to use pysops on visiting senators in an effort to secure increased funding for the war, an illegal act; only a few days prior, CENTCOM spokesmen were confidently telling the public that such other psychological capabilities as persona management would never be used on Americans as that would be illegal. The fact is that such laws have been routinely broken by the military and intelligence community, who are now been joined in this practice by segments of the federal contracting industry.
It is inevitable, then, that such capabilities as form the backbone of Romas/COIN and its replacement Odyssey will be deployed against a growing segment of the world's population. The powerful institutions that wield them will grow all the more powerful as they are provided better and better methods by which to monitor, deceive, and manipulate. The informed electorate upon which liberty depends will be increasingly misinformed. No tactical advantage conferred by the use of these programs can outweigh the damage that will be done to mankind in the process of creating them.
The complete Project PM announcement about Romas/COIN has been published: http://wiki.echelon2.org:8090/wiki/Romas/COIN

 Homepage:
Homepage:

Comments
Hide the following comment
A sinister cyber-surveillance scheme exposed
23.06.2011 11:25
"In the councils of government, we must guard against the acquisition of unwarranted influence, whether sought or unsought, by the military-industrial complex. The potential for the disastrous rise of misplaced power exists and will persist."
Sixty years later, the military-industrial complex has been joined by another unprecedented centre of what has increasingly proven to be "misplaced power": the dozens of secretive firms known collectively as the intelligence contracting industry.
Last February, three of these firms – HBGary Federal, Palantir and Berico, known collectively as Team Themis – were discovered to have conspired to hire out their information war capabilities to corporations which hoped to strike back at perceived enemies, including US activist groups, WikiLeaks and journalist Glenn Greenwald. That such a dangerous new dynamic was now in play was only revealed due to a raid by hackers associated with the Anonymous collective, resulting in the dissemination of more than 70,000 emails to and from executives at HBGary Federal and its parent company HBGary.
After having spent several months studying those emails and otherwise investigating the industry depicted therein, I have revealed my summary of a classified US intelligence programme known as Romas/COIN, as well as its upcoming replacement, known as Odyssey. The programme appears to allow for the large-scale monitoring of social networks by way of such things as natural language processing, semantic analysis, latent semantic indexing and IT intrusion. At the same time, it also entails the dissemination of some unknown degree of information to a given population through a variety of means – without any hint that the actual source is US intelligence. Scattered discussions of Arab translation services may indicate that the programme targets the Middle East.
Despite the details I have provided in the document – which is also now in the possession of several major news outlets and which may be published in whole or in part by any party that cares to do so – there remains a great deal that is unclear about Romas/COIN and the capabilities it comprises. The information with which I've worked consists almost entirely of email correspondence between executives of several firms that together sought to win the contract to provide the programme's technical requirements, and because many of the discussions occurred in meetings and phone conversations, the information remaining deals largely with prospective partners, the utility of one capability over another, and other clues spread out over hundreds of email exchanges between a large number of participants.
The significance of this programme to the public is not limited to its potential for abuse by facets of the US intelligence community, which has long been proverbial for misusing other of its capabilities. Perhaps the most astonishing aspect is the fact that the partnership of contracting firms and other corporate entities that worked to obtain the contract was put into motion in large part by Aaron Barr, the disgraced former CEO of HBGary Federal who was at the centre of Team Themis's conspiracy to put high-end intelligence capabilities at the disposal of private institutions. As I explain further in the linked report, this fact alone should prompt increased investigation into the manner in which this industry operates and the threats it represents to democratic institutions.
Altogether, the existence and nature of Romas/COIN should confirm what many had already come to realise over the past few years, in particular: the US and other states have no intention of allowing populations to conduct their affairs without scrutiny. Such states ought not complain when they find themselves subjected to similar scrutiny – as will increasingly become the case over the next several years.
Barrett Brown
 Homepage:
http://www.guardian.co.uk/commentisfree/cifamerica/2011/jun/22/hacking-anonymous
Homepage:
http://www.guardian.co.uk/commentisfree/cifamerica/2011/jun/22/hacking-anonymous